We live in a world where IT departments are incredibly complex and identifying security breaches or events fast is crucial to slowing down and stopping the impact of them. But what is needed to detect and stop attacks in this environment?
Security teams need appropriate tools to process and correlate huge amount of historical and real-time security data, and by applying expert analytics techniques to these substantial amounts of data, information security teams can defend against and even prevent even the most sophisticated data breaches.
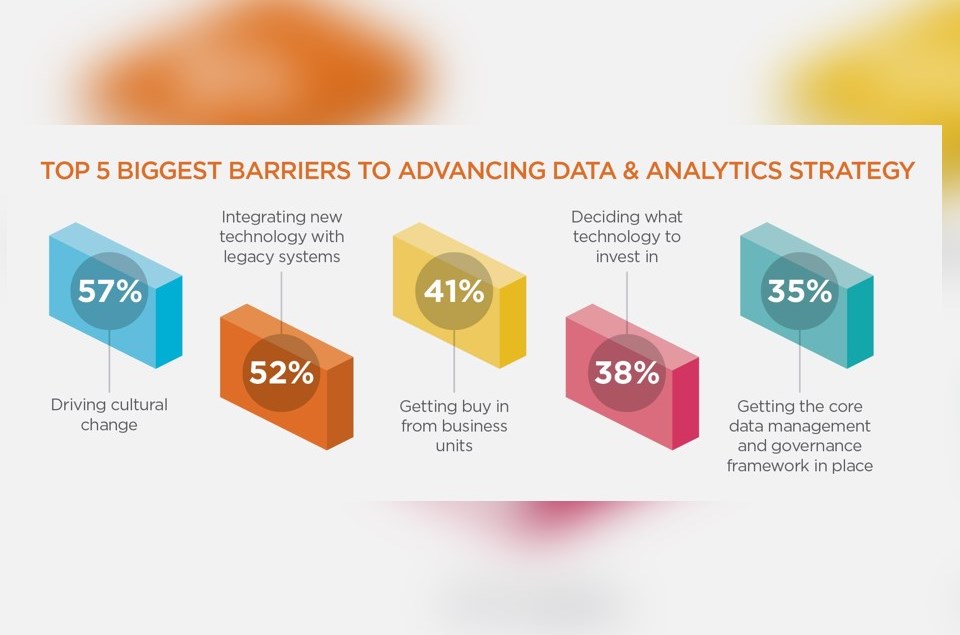
How can Data, Analytics and Cyber Security Work Together Successfully?
Successfully getting data, analytics and cyber security to work together seamlessly can often be challenging. Due to the large amount of attack vectors, as well as the copious amounts of data to go through, getting the right insight for data security can be difficult. According to recent research by Verizon, preventing one kind of data security attack is not adequate, as attackers often use a variety of techniques during their campaigns. It is estimated that around 62% of attacks are linked to hacking, with 51% making use of malware and 43% making use of social media to deploy attacks. Interestingly, 14% of attacks were deemed to be the result of employee mistakes which often led to holes in security that were exploited.
Cyber criminals have also started to make use of artificial intelligence inside their own systems to scale attacks, make phishing emails much more personalized, identify system vulnerabilities and change ransomware and malware in real time. Outsmarting these complex attacks requires highly skilled cyber security teams to monitor networks for a wide range of threats, and on many occasions these threats may or may not follow traditional threat patterns.
If data is used to stay ahead of potential threats, this can help. Many enterprise level companies have substantial amounts of data at their disposal coming in from a diverse set of sources including network infrastructure and server logs, application logs, intrusion detection systems and many more. This data quickly adds up for large enterprises often petabytes in size.
Threat response teams need to run queries, often in real time, when a suspicious threat is found and run those queries against large streaming and historical data sets to check the extent of a possible data breach. This detailed analysis should confirm the threat, flag it up as requiring more investigation, or discount it. This means an enterprise should have enough processing power to analyze billions of records within a matter of seconds.
How can using these large volumes of data be stopped?
While many large enterprises have Security Information and Event Management (CIEM) platforms and would use these to manage all this data, many of these solutions were not constructed with large volumes of data in mind. These threat detection platforms produce petabytes of data that needs to be analyzed and contextualized, often in real time, but to process these petabytes of data significant computing power is required. Many SIEM and security analytics tools were built to be used on-premise but scaling these to meet today’s data demands can often be very costly.
Many security teams often have access to only a few weeks’ worth of historical data, as storing substantial amounts of data at scale can often be expensive. When a security breach happens analysts often must undertake thorough historic analyses to investigate the size and scope of an attack. In addition, another challenge often encountered by security teams is the large amount of false positives produced by SIEM tools. As so much data is often captured in cloud infrastructure logs, intrusion detection systems, OS logs and other such monitoring devices, hundreds of suspicious events can often be detected every day, and this begins a lengthy and time-consuming process to determine which of these threats are legitimate.
Conclusion
The issues around data, analytics and cyber security working together are not insurmountable. Enterprises might consider cloud-based solutions to get over the challenges of data processing and storage and can help make processing copious amounts of data more streamlined. Augmenting existing CIEM solutions with data platforms that are capable of modeling diverse sets of data at scale helps extend visibility and improves the overall security of enterprises.
The use of AI is another area that data science is leaning on along with machine learning to prioritize security alerts and automate responses to significantly reduce the stress placed on security teams. Machine learning models can be trained to identify unusual behavior patterns that may not be picked up by pre-set security rules, and security teams who are looking to make use of AI and machine learning need to invest heavily in data science applications and skillsets.
The ultimate aim is to make it easier for analysts, security teams and IT professionals to collaborate in a centralized data environment to improve speed-to-insight and processes, and bringing a data approach along with choosing the right data platform to help solve these challenges opens the door to better data attack prevention and a more secure enterprise from data, analytics and cyber security professionals all working together.